How to disable TLS1.0 and TLS1.1 protocols to keep the server more secure? Regardless of whether it is a linux or windows server, we recommend closing the tls1.0 protocol. You can also disable TLS1.0 and TLS1.1 in NGINX to make your website more secure.
How to disable TLS1.0 and TLS1.1 protocols
SSL has been proven insecure due to vulnerabilities discovered in the past. The difference between TLS1.0 and SSL3.0 is actually not too much, and TLS1.0 can be forced to be downgraded to SSL3.0 in some ways.
As a result, the Payment Card Industry Security Standards Committee (PCI SSC) forcibly canceled the payment card industry’s support for TLS 1.0, and strongly recommends the cancellation of TLS 1.1 support.
Apple, Google, Microsoft, and Mozilla have also issued statements that they will give up support for TLS 1.1 and TLS 1.0 in early 2020. The reason is that these two versions use outdated algorithms and encryption systems. It has been found that these algorithms and systems are very fragile, such as SHA-1 and MD5. They also lack modern features like perfect forward secrecy and are vulnerable to downgrade attacks.
SSL/TLS version
| protocol | release time | state |
|---|---|---|
| SSL 1.0 | Unannounced | Unannounced |
| SSL 2.0 | the year 1995 | Deprecated in 2011 |
| SSL 3.0 | year 1996 | Deprecated in 2015 |
| TLS 1.0 | Year 1999 | Planned to be deprecated in 2020 |
| TLS 1.1 | year 2006 | Planned to be deprecated in 2020 |
| TLS 1.2 | Year 2008 | |
| TLS 1.3 | 2018 |
Nginx
- Usually Nginx
conf/nginx.confconfiguration is as follows
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
- Delete
TLS1.0 TLSv1.1, add TLS1.3
ssl_protocols TLSv1.2 TLSv1.3;
How to disable TLS1.0 and TLS1.1 protocols to keep the server more secure
- Restart Nginx for the configuration to take effect
nginx -s reload
Apache
- Usually the configuration of Apache is as follows
SSLProtocol -ALL +TLSv1 +TLSv1.1 +TLSv1.2
1-1. RedHat-based distribution (CentOS, Fedora) configuration file /etc/httpd/conf/httpd.conf
How to disable TLS1.0 and TLS1.1 protocols to keep the server more secure
1-2. Debian-based distribution (Ubuntu) configuration file /etc/apache2/sites-enabled/ directory Down
- Delete
+TLSv1 +TLSv1.1and add TLSv1.3
SSLProtocol -ALL +TLSv1.2 +TLSv1.3
How to disable TLS1.0 and TLS1.1 protocols to keep the server more secure
- Restart Apache for the configuration to take effect
# CentOS,Fedora systemctl restart httpd # Ubuntu service apache2 restart
How to disable TLS1.0 and TLS1.1 protocols to keep the server more secure
IIS server
- The IIS server needs to use the official tool ( IISCrypto.exe ) to modify
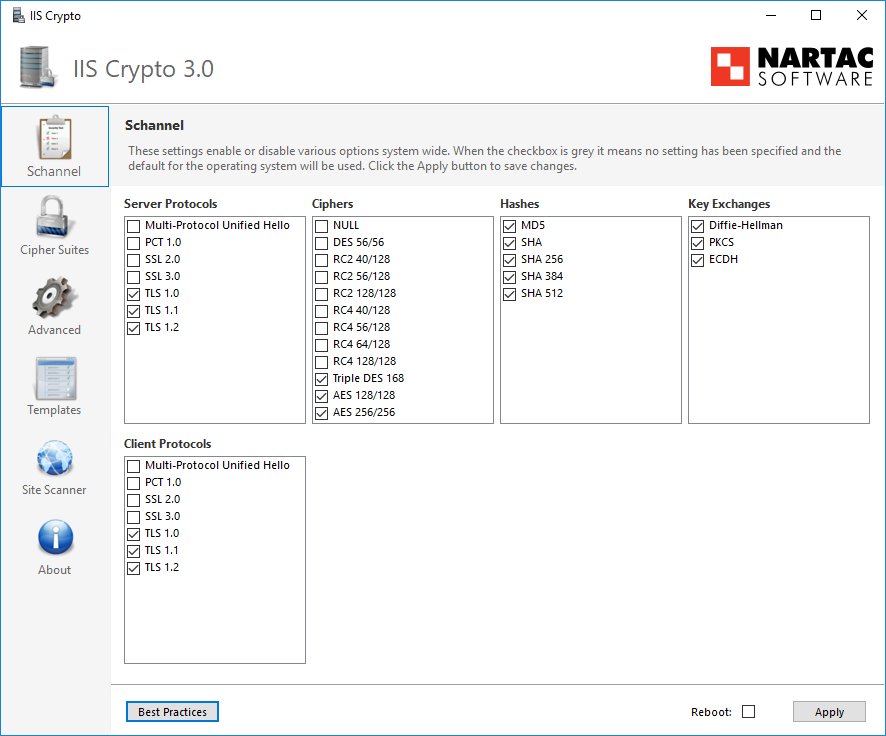
IISCrypto.exe
Tomcat
- Usually Tomcat
conf/server.xmlconfiguration is as follows
SSLProtocol="TLSv1+TLSv1.1+TLSv1.2"
- Delete
+TLSv1 +TLSv1.1, add TLS1.3
SSLProtocol="TLSv1.2+TLSv1.3"
- Restart Tomcat for the configuration to take effect
# close tomcat bin/shutdown.sh # startup tomcat bin/startup.sh
- Note: The above servers need to rely on the version of openSSL and the support of IIS and Java to increase TLS1.3
Detect
1. Test the TLS1.0 protocol
openssl s_client -connect www.znlive.com:443 -tls1 < /dev/null
CONNECTED(00000003)
write:errno=104
---
no peer certificate available
---
No client certificate CA names sent
---
SSL handshake has read 0 bytes and written 0 bytes
---
New, (NONE), Cipher is (NONE)
Secure Renegotiation IS NOT supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1
Cipher : 0000
Session-ID:
Session-ID-ctx:
Master-Key:
Key-Arg : None
Krb5 Principal: None
PSK identity: None
PSK identity hint: None
Start Time: 1633685489
Timeout : 7200 (sec)
Verify return code: 0 (ok)
---
- Note: Indicates that the connection using the TLS1.0 protocol is unavailable, indicating that we have disabled TLS1.0
Two, test the TLS1.2 protocol
openssl s_client -connect www.znlive.com:443 -tls1_2 < /dev/null
CONNECTED(00000003)
depth=3 O = Digital Signature Trust Co., CN = DST Root CA X3
verify error:num=10:certificate has expired
notAfter=Sep 30 14:01:15 2021 GMT
---
Certificate chain
0 s:/CN=jhrs.com
i:/C=US/O=Let's Encrypt/CN=R3
1 s:/C=US/O=Let's Encrypt/CN=R3
i:/C=US/O=Internet Security Research Group/CN=ISRG Root X1
2 s:/C=US/O=Internet Security Research Group/CN=ISRG Root X1
i:/O=Digital Signature Trust Co./CN=DST Root CA X3
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIFMzCCBBugAwIBAgISA7VcG2st4Mb9oRuhffYzViI9MA0GCSqGSIb3DQEBCwUA
MDIxCzAJBgNVBAYTAlVTMRYwFAYDVQQKEw1MZXQncyBFbmNyeXB0MQswCQYDVQQD
EwJSMzAeFw0yMTA5MzAxNTE5MjhaFw0yMTEyMjkxNTE5MjdaMCExHzAdBgNVBAMT
4C7vbju3QzFzUyiu8Y3Si2V5oJbzrhIlftqQUUTU2vmMO1lmQi/uD3IqOfZZ4VXL
dcOIHmUVDAzLOMa2brg8YXSQatARlhYDjC1T2aSPMxaKjKq84SHKw67PI6PGGE0u
uYYizdj0riGDsULplmX/u7pFcaw6WjH9lBAasJqxGwFAeJ7AyK2N4D+WPz+fefsw
IAaGUCj2G8pFoKl0N5DVzqgFIWwIxrfYYqS4ogqRUFsgZpcUuTj6
-----END CERTIFICATE-----
subject=/CN=znlive.com
issuer=/C=US/O=Let's Encrypt/CN=R3
---
No client certificate CA names sent
Peer signing digest: SHA512
Server Temp Key: ECDH, P-256, 256 bits
---
SSL handshake has read 4702 bytes and written 415 bytes
---
New, TLSv1/SSLv3, Cipher is ECDHE-RSA-AES128-GCM-SHA256
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES128-GCM-SHA256
Session-ID: C617C1E0D6945124100508852C5249DFD8D67F9312104C55547887B9CFD903
Session-ID-ctx:
Master-Key: 3A0F9459A936B9DC12E7F60ACF67E4B7006D950494F10AE1192E37AD4A732BA3D072EB1E0B9F317710CEAB8FAA1
Key-Arg : None
Krb5 Principal: None
PSK identity: None
PSK identity hint: None
TLS session ticket lifetime hint: 300 (seconds)
TLS session ticket:
0000 - ca 53 6c fd 08 46 6e c4-3f 4f 25 43 70 22 c7 95 .Sl..Fn.?O%Cp"..
0010 - cb 45 ec fd 7c 1d 49 28-58 81 e0 4d c2 bd d1 7b .E..|.I(X..M...{
0020 - 0c 23 42 0c c4 4d 58 f2-68 a7 0b a3 50 b0 ec e0 .#B..MX.h...P...
0030 - 7e 57 a1 6d 16 44 5b db-90 91 f1 2c 44 bf d9 78 ~W.m.D[....,D..x
0040 - c8 24 ea 0a e7 c6 55 b0-e2 42 6c 2c 49 7c 05 64 .$....U..Bl,I|.d
0050 - 33 91 48 9a a8 0f 97 8a-c7 06 4d ed 85 8b d2 48 3.H.......M....H
00a0 - 8a 8c 90 1c 8f 21 1b ad-37 61 00 b1 b4 fd 49 7b .....!..7a....I{
Start Time: 1633686054
Timeout : 7200 (sec)
Verify return code: 10 (certificate has expired)
---
DONE
- Note: indicates that the connection is passed using the TLS1.2 protocol, indicating that we have disabled TLS1.2
3. Third-party evaluation websites